Setup GCP credential for scanning
Create Security Audit Role
- Log into your Google Cloud console and "Activate" your Cloud Shell.
- Create a new file called security-audit-role.yaml. You can use:
nano meghops-security-scanner-role.yaml. - Copy and paste the following yaml code in the file on your Cloud Shell, press Ctrl + X and type "Y" to save the file.
name: roles/MeghOpsSecScanRole
title: MeghOps Security Scanner Role
includedPermissions:
- cloudasset.assets.listResource
- cloudkms.cryptoKeys.list
- cloudkms.keyRings.list
- cloudsql.instances.list
- cloudsql.users.list
- compute.autoscalers.list
- compute.backendServices.list
- compute.disks.list
- compute.firewalls.list
- compute.healthChecks.list
- compute.instanceGroups.list
- compute.instances.getIamPolicy
- compute.instances.list
- compute.networks.list
- compute.projects.get
- compute.securityPolicies.list
- compute.subnetworks.list
- compute.targetHttpProxies.list
- container.clusters.list
- dns.managedZones.list
- iam.serviceAccountKeys.list
- iam.serviceAccounts.list
- logging.logMetrics.list
- logging.sinks.list
- monitoring.alertPolicies.list
- resourcemanager.folders.get
- resourcemanager.folders.getIamPolicy
- resourcemanager.folders.list
- resourcemanager.hierarchyNodes.listTagBindings
- resourcemanager.organizations.get
- resourcemanager.organizations.getIamPolicy
- resourcemanager.projects.get
- resourcemanager.projects.getIamPolicy
- resourcemanager.projects.list
- resourcemanager.resourceTagBindings.list
- resourcemanager.tagKeys.get
- resourcemanager.tagKeys.getIamPolicy
- resourcemanager.tagKeys.list
- resourcemanager.tagValues.get
- resourcemanager.tagValues.getIamPolicy
- resourcemanager.tagValues.list
- storage.buckets.getIamPolicy
- storage.buckets.list
stage: GA
Run the following command to create the role, use your Organization Id to create the Role at the Org Level:
gcloud iam roles create MeghOpsSecScanRole --organization=YOUR_ORGANIZATION_ID --file=meghops-security-scanner-role.yamlOR - If you don't have access to the GCP cloud shell then manually create the role with the above permission
- Goto Google cloud console and select the project you want to use
- From the left navigation menu select
IAM & Admin->Roles - Now click on
Create Role - Then put
Title,Description, andIDthen click onAdd Permissionsit'll open a dialog to select the available permissions - Select all the permission mentioned above, after adding these permission click on
Createto create the role.
Create Service Account
- Log into your Google Cloud console and navigate to IAM Admin > Service Accounts.
- Click on "Create Service Account".
- Enter a name in the "Service account name" and description.
- Click on Continue.
- Select the role: Custom > MeghOps Security Scanner Role.
- Click on Continue.
- Click on "Create Key".
- Leave the default JSON selected.
- Click on "Create".
- The key will be downloaded to your computer.
Now let's add this credential to MeghOps
- Goto https://app.meghops.com/auth/login and login with your account
- Now go to settings by clicking top right corner ( Profile avatar) then
Settings
- From the
settingspage go toCloud accountsthen click onAdd credential. - Now from this dialog select
GCPand checkmark onScanor if you want to use the same account for scan and cost then checkmark these two, now paste your GCP credential JSON then click onSubmit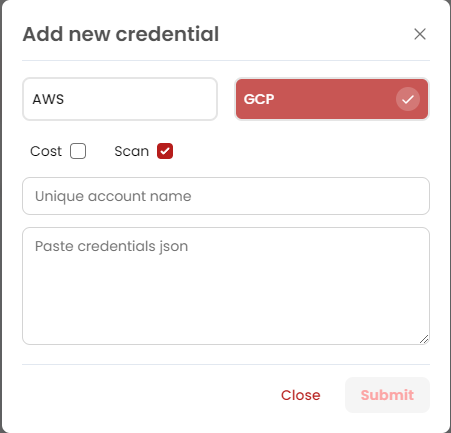
- Done!